SHARED RESPONSIBILITY MODEL
Introduction
Security and Compliance is a shared responsibility between Angani and the customer. This policy outlines the responsibilities of both Angani and our clients in safeguarding data hosted on our cloud platform.
Angani’s commitment
- Data Security: We are committed to implementing robust security measures on a physical, host virtualization and network level to protect data stored on our cloud platform from unauthorized access, disclosure, alteration, and destruction.
- Compliance: We adhere to relevant data protection regulations, industry standards, and best practices to ensure the confidentiality, integrity, and availability of our clients’ data.
- Transparency: We provide clear and transparent guidelines on our security practices, including data encryption, access controls, and incident response procedures.
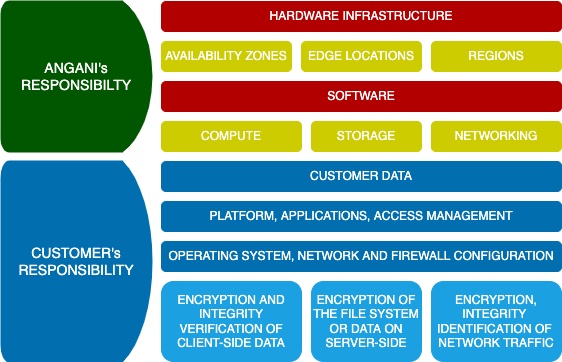
Shared Responsibilities
Angani’s Responsibilities
- Infrastructure Security: We are responsible for securing the underlying cloud infrastructure, including network, storage, and computing resources.
- Data Encryption: We implement encryption mechanisms to protect data both in transit and at rest within our cloud environment.
- Access Controls: We manage access controls to the cloud platform, ensuring that only authorized personnel can access sensitive data and resources.
- Monitoring and Logging: We continuously monitor the cloud environment for suspicious activities and maintain audit logs to track access and changes to data.
- Incident Response: We have established procedures for responding to security incidents, including timely notifications to affected clients and relevant authorities.
Client’s Responsibilities
- Data Classification: Clients are responsible for classifying their data and determining the appropriate level of protection based on sensitivity and regulatory requirements.
- Updates and security patches: Customers are responsible for the management of the guest operating system including updates and security patches, any application software or utilities installed by the customer on the instances, and the configuration of the firewall on each instance.
- User Access Management: Clients are responsible for managing user access within their organization and enforcing strong authentication mechanisms.
- Data Encryption: Clients are responsible for encrypting sensitive data before uploading it to the cloud platform and managing encryption keys securely.
- Security Configuration: Clients are responsible for configuring security settings within their cloud environment, including firewall rules, access policies, and security groups.
- Monitoring and Compliance: Clients are responsible for monitoring their cloud environment for security threats and ensuring compliance with relevant regulations and standards.
Collaboration and Communication
We recognize that effective collaboration and communication between Angani and our clients is essential for ensuring the security of data hosted on our cloud platform. Therefore, we are committed to:
- Providing regular updates on security best practices and emerging threats.
- Offering support and guidance to clients in implementing security measures within their cloud environment.
- Facilitating audits and assessments to verify compliance with shared responsibilities as an add-on service.
Conclusion
By adhering to this shared responsibility model, we aim to create a secure and trusted cloud environment where our clients can confidently store and manage their data. We remain committed to continuously improving our security practices and working collaboratively with our clients to mitigate risks and protect sensitive information.